Ransomware Anatomy Of An Attack Technology Signals
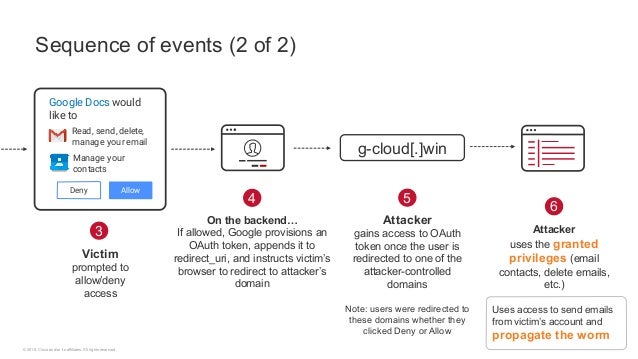
Chapter 12 Anatomy Of An Attack Ppt Video Online Download
 How Malware Works Anatomy Of An Attack In Five Stages
How Malware Works Anatomy Of An Attack In Five Stages
 Hospital In Security Anatomy Of An Attack At Montreal
Hospital In Security Anatomy Of An Attack At Montreal
 Anatomy Of An Attack Kucoin Telegram Channel Compromise
Anatomy Of An Attack Kucoin Telegram Channel Compromise
Infographic The Anatomy Of An Anonymous Attack Computer
 Anatomy Of An Attack How Clouds Get Hacked
Anatomy Of An Attack How Clouds Get Hacked
 Cyberthreat Evolution Proactive Detection Prevention
Cyberthreat Evolution Proactive Detection Prevention
 185990691 Anatomy Of An Attack Anatomy Of A Cyber Attack
185990691 Anatomy Of An Attack Anatomy Of A Cyber Attack
 Anatomy Of An Attack New York And Toronto Naked Security
Anatomy Of An Attack New York And Toronto Naked Security

The Anatomy Of An Attack In The World Of Open Source
 Anatomy Of An Ntp Reflection Attack Source Arbor Networks
Anatomy Of An Ntp Reflection Attack Source Arbor Networks
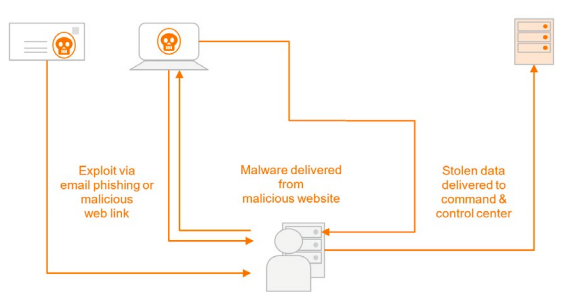 White Paper Enabling Adaptive Security With Advanced
White Paper Enabling Adaptive Security With Advanced
 The Anatomy Of A Cybersecurity Attack
The Anatomy Of A Cybersecurity Attack
 Brute Force Anatomy Of An Attack
Brute Force Anatomy Of An Attack
 The Anatomy Of An Attack Surface Riskiq
The Anatomy Of An Attack Surface Riskiq
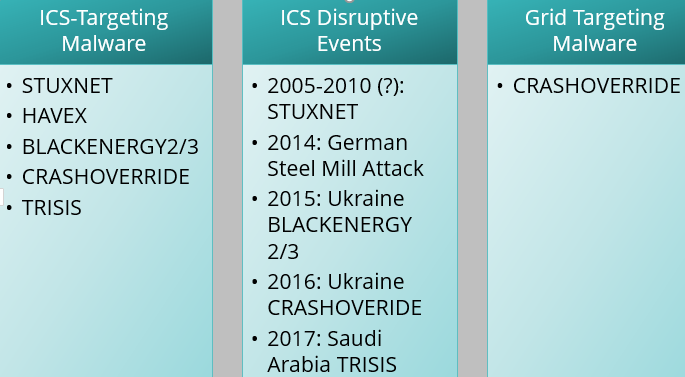 Virus Bulletin Vb2018 Paper Anatomy Of An Attack
Virus Bulletin Vb2018 Paper Anatomy Of An Attack
 Anatomy Of An Attack Zero Day Exploit
Anatomy Of An Attack Zero Day Exploit
 Yahoo Anatomy Of A Cyber Attack Interset Medium
Yahoo Anatomy Of A Cyber Attack Interset Medium
World Trade Center Anatomy Of An Attack
 The Anatomy Of An 808 Sample Attack Kick Body And Tail Plus Tips On Improving Your 808 Mixing
The Anatomy Of An 808 Sample Attack Kick Body And Tail Plus Tips On Improving Your 808 Mixing
The Anatomy Of An Attack Bai Security It Security
 4 Stages Of An Attack Visual Ly
4 Stages Of An Attack Visual Ly
 Infographic Anatomy Of A Web Application Attack Owasp Top
Infographic Anatomy Of A Web Application Attack Owasp Top
 Cisco Anatomy Of An Attack Casimir Effect
Cisco Anatomy Of An Attack Casimir Effect
 Exclusive Healthcare Webinar Anatomy Of An Email Borne Attack
Exclusive Healthcare Webinar Anatomy Of An Email Borne Attack
 Anatomy Of An Xss Attack Pixel Jar
Anatomy Of An Xss Attack Pixel Jar



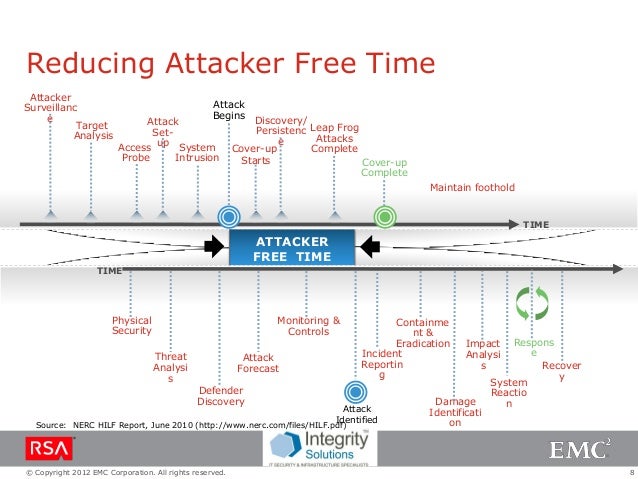


Posting Komentar
Posting Komentar